Secure or Sunk
In crypto, $2.7B vanished to hacks and scams in six months. That is not a market quirk. It is a build culture problem. Security is not a later task. It is day-zero infrastructure.

2025 saw a spike in major incidents across exchanges and protocols. Over 50 large exploits hit the ecosystem. The standout was the Bybit breach, about 400,000 ETH (~$1.45B) drained from a centralized exchange after attackers tampered with a wallet UI used by multisig signers. That single outlier dominated totals. Add the $223M Sui Cetus overflow exploit and the LIBRA insider rug on Solana (retail losses estimated near $250M) and you have a volatile half year. It was not just degen farms getting clipped. Core infrastructure, governance, and operational controls failed under pressure. The signal to founders is simple: build secure, or you will trend for the wrong reason.
What is actually going wrong? Patterns repeat. The human and operational layer sits at the root of most damage. Key compromises, phishing, compromised build or UI pipelines, sloppy admin roles, and insider actions are common. Phishing losses jumped. Social engineering scaled with AI. Technical flaws still caused damage, with Cetus losing $223M to a math overflow in a shared library, but pure code bugs were a smaller slice of the total than governance and access failures. The worst heists blended multiple weaknesses: infrastructure compromise, trust abuse, and process gaps.
The industry’s security stack still lags. There is no widely enforced baseline for smart contract and operational security. OWASP Smart Contract Top 10 exists, but adoption is inconsistent. Audits are too often treated as a checkbox rather than a living process. Teams fork code without re-auditing. Automated scanners and runtime monitors can catch known issues and strange behavior, but they are underused or not integrated into CI/CD. These gaps are direct paths to losses, downtime, and trust collapse.
(Below is a founder-first playbook with immediate changes to make, followed by an investor guide on what to look out for.)
What founders need to do now
1) Treat keys, signers, and admin paths like crown jewels.
Use multisig or MPC for treasury and privileged actions.
Lock down the interfaces signers use, and harden build pipelines and front ends to prevent injected parameters or malicious code. The Bybit case showed signers can be tricked if the UI is compromised.
Enforce hardware wallets, strong 2FA, IP allowlists, and session limits for critical operations.
Apply least privilege across infrastructure, cloud, on-chain roles, and admin dashboards. Rotate, monitor, and expire credentials.
Separate environments: isolated machines for deployers, cold storage with withdrawal limits and time-locks for treasuries.
2) Bake security checks into your code path.
Add automated static analysis (multiple tools, not one) to your CI so every pull request is scanned for known anti-patterns. Treat false positives as triage, not excuses.
Run property-based tests, fuzzers, and differential tests for critical math and accounting logic.
Use runtime anomaly detection and on-chain monitoring to spot abnormal flows in minutes, not days. Alerts must page humans with the authority to act.
3) Engineer for failure, then practice.
Build circuit breakers, rate limits, time-locks, and pause mechanisms around sensitive functions and outflows.
Establish withdrawal queues or delays where feasible to buy response time.
Write and rehearse an incident playbook: who gets paged, who can pause, who communicates, recovery steps, and user communication templates.
4) Avoid the SaaS trap.
Many early-stage teams lean on free or low-cost SaaS hosting, deployment, and site-building platforms to move fast. The advanced logging, audit trails, and access controls needed once you handle real funds often sit behind enterprise plans. At that point you either pay heavily to upgrade, spend precious cycles re-platforming, or build fragile work-arounds under pressure. Bake this into your roadmap. If you know you will need high-fidelity logs, granular role controls, or incident forensics, choose tools and plans that can deliver them before you are in a crisis.
5) Close cross-chain blast radius.
Bridges and messaging layers are high-value targets. Prefer proven options. For significant value flows, compose multiple bridges and require combined validation to avoid single points of failure.
Track upstream advisories. A partner bridge upgrade or endpoint outage can cascade into your app.
Validate assumptions in your threat model: what happens if oracles halt, a relayer stalls, or a verifier set rotates unexpectedly.
6) Move from audit to continuous assurance.
Pre-launch: multiple independent reviews for critical components.
Post-launch: re-audits for material changes and ongoing bug bounties with clear scope and fast payouts.
Hire or contract a security lead with authority to block risky launches.
7) Show your work.
Publish audit artifacts, list key management practices, and describe your upgrade and pause mechanics.
Be transparent during incidents. Fast facts and user remediation beat silence.
Context, not confusion: the numbers
Totals in security reports mix categories that overlap. An "infrastructure compromise" can also be an "access control failure." Don't sum categories as if they're disjoint sets. For H1 2025, the Bybit CEX breach (~$1.45B) heavily skews any category it's assigned to. That doesn't negate the trend - human-in-the-loop and process failures caused outsized damage - but you should read stack charts with care. The right takeaway is: operational discipline is the highest-ROI security investment, not "X vector alone cost $1.3B and Y vector cost $1.45B independently."
A few corrected specifics to anchor your mental model:
Bybit: 400k ETH ($1.45B). CeFi breach via compromised UI/infra affecting multisig approvals.
LIBRA (Solana): insiders realized ~$100M profit; estimated ~$250M retail losses.
Phemex: hot-wallet loss initially quoted around $70-73M; later tallies raised it toward ~$85M as tracking firm attributions updated.
Cetus (Sui): ~$223M drained via integer overflow in a shared math path; validators reportedly froze a large fraction post-incident.
Use these as case studies, not just headlines: each one maps to a concrete fix in the playbook above.
Case studies
CoinDCX: malware + hot wallet exposure (~$44M).
Takeaway: the weakest link can be a compromised build, endpoint, or server - not just a contract. Secure signing environments and supply-chain integrity matter as much as solidity.
BigONE: supply-chain tampering (~$27M).
Takeaway: internal server tamper let unauthorized withdrawals through. Monitoring and change-control on infra is as critical as on-chain guards.
Malicious VSCode Extensions: supply-chain compromise (229M+ installs).
Takeaway: polished, high-download IDE extensions can ship malicious code undetected. Audit tools, limit permissions, and treat your dev environment like prod.
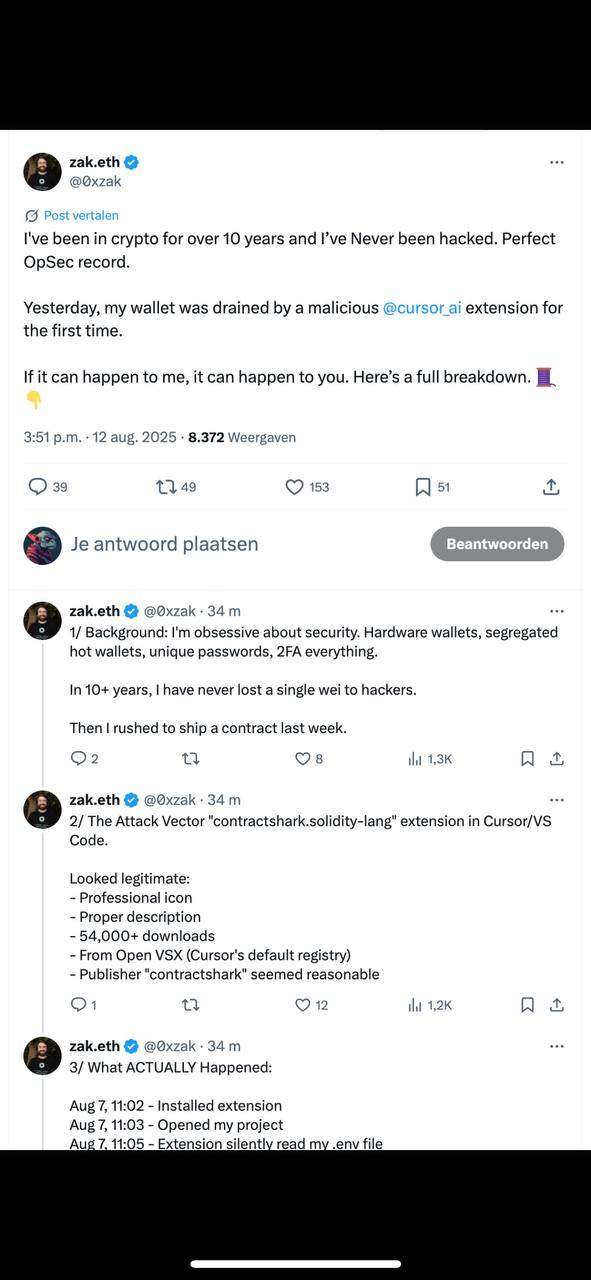
Zak.eth Hack: poisoned IDE plugin (~thousands of drained wallets).
Takeaway: even seasoned builders can get burned by trusted-looking extensions. Vet every dependency, watch for silent file reads, and keep secrets isolated from your editor.
Meta-pattern: it's rarely a single bug. It's exploit chains, a small misstep at one layer compounding with a governance blind spot at another.
Founder FAQ:
Do we need "all the scanners"?
No. You need redundancy. Pair a strong static analyzer with a second engine for coverage diversity, add fuzzing for state-space gaps, and add runtime detectors to catch economic attacks and abnormal flows. Wire them to CI and paging.
Are time-locks and pauses anti-UX?
Time-locks on governance changes and superuser actions protect users without hurting day-to-day UX. Pauses and rate limits should be targeted and temporary, with clear playbooks.
Do we still need multiple audits?
For critical systems: yes. Independent eyes find different classes of issues. Then shift budget to continuous assurance. Audits are snapshots; attackers operate in video.
How do we avoid "over-engineering" security?
Tie controls to asset at risk and threat model. Treasury? Fortify. Periphery? Right-size. Document trade-offs; revisit quarterly as TVL and usage change.
Investor and ecosystem lens
Your best due-diligence filter today isn't "was it audited?" It's how the team runs security as a system.
Ask for proof, not promises:
Key stewardship: who can move treasury? What devices and policies protect them? How many distinct parties?
Change control: how are upgrades proposed, reviewed, approved, executed? Time-locks? Multisig policies? Rollback plans?
Runtime defense: what on-chain monitors exist? What alerts page humans? Who has authority to pause and how fast?
Dependency risk: which bridges, oracles, verifiers, and libraries are in use? What's the contingency if one fails or is attacked?
Posture transparency: recent audit dates, bounty programs, incident playbook, and evidence they've rehearsed it.
Green flags: explicit key policies, CI-enforced scanners, incident drills, measured use of circuit breakers, transparent audit history, and a security lead with veto power over risky launches. Red flags: one-and-done audit PDFs, single signer anywhere near treasury, forks without fresh reviews, no monitoring, and vague answers about who can hit "pause."
Ecosystems should align incentives accordingly: grants and spotlight for teams with mature security posture, not just shiny demos. Security-weighted scoring in incubators, quests, and hackathons pushes culture in the right direction.
Forecast: where security spend is going next
Runtime first. More teams will treat on-chain monitoring and anomaly detection as table stakes, especially for high-TVL systems. The goal is minutes to mitigation, not days to post-mortem.
Composed interoperability. High-value apps will migrate to multi-bridge designs, distributing trust across independent verifiers. Standards that enable composition will gain adoption.
Continuous assurance platforms. Expect "SecOps for smart contracts" to feel like modern DevOps, policy-gated upgrades, automated guardians, and integrated scanners as pipelines, not side quests.
Governance hardening. More projects will implement formal upgrade processes, stronger quorums, staged rollouts, and emergency controls that are tested, not theoretical.
Talent and training. The market will reward teams who can prove they practice security, not just talk about it, engineers who can reason about both protocol mechanics and operational reality.
A big shout out to Credshields who helped inspire us to write this.
📰 Ecosystem Headlines
Wallet Hacks & Phishing Dominate 2025: A CertiK report shows crypto lost $2.47B in H1 2025 to security incidents, with $1.7B from wallet breaches (just 34 attacks!) and $410M from phishing scams . The largest hack was the $1.5B Bybit exploit linked to North Korea , highlighting how even big exchanges are vulnerable. In short: personal OPSEC and key management are more crucial than ever.
OpenBridge for Cross-Chain Security: OpenZeppelin and Axelar launched OpenBridge, an open-source framework built on the new ERC-7786 standard . It lets devs integrate multiple bridges in one and compose extra security for high-value cross-chain transactions. Essentially, you’re no longer tied to one bridge’s trust model – you can use many and require combined validation. As cross-chain exploits mount, this composability could be a game-changer for building safer multichain dApps.
🔗 www.axelar.network
Regulators Eye Web3 Security Standards: In a notable move, the U.S. government set up a Strategic Cryptocurrency Reserve and the SEC launched a Crypto Task Force . The goal: to foster clearer, innovation-friendly regulations that address the Wild West security environment in crypto. This comes alongside calls for industry-wide standards (think OWASP for crypto). For founders, it’s a sign that security compliance will likely become a prerequisite for mainstream adoption – better to get ahead of the curve now.
🛠 Builder’s Corner
SolidityScan by CredShields – An AI-powered vulnerability scanner for smart contracts, boasting 450+ detectors for common pitfalls . It’s like having a junior auditor on call 24/7, surfacing issues from reentrancy to integer bugs before you even hit deploy. Tip: integrate it into your GitHub Actions or CI pipeline, so every commit gets a security once-over.
Forta Network – A decentralized monitoring network that acts like a blockchain burglar alarm. Forta’s bots watch over $40B+ in on-chain assets and use machine learning to detect suspicious activity in real time . In the Euler Finance hack, Forta flagged the attack before funds were drained – giving a vital few minutes warning. Builders can subscribe to Forta alerts or write custom detection bots for their own protocols, turning on the lights for when the bad guys come.
OpenZeppelin Defender – A security operations (SecOps) platform for managing and automating smart contract admin tasks. Defender helps you secure upgrade workflows, manage role-based access, and set up multi-sig approvals with ease. Use it to schedule timelocked upgrades, automate pause/unpause scripts during incidents, and generally ensure your “god mode” functions are never a single point of failure. It’s like DevOps, but for keeping your contracts safe and sane post-deployment.
📢 Cracked Labs Spotlight
Dreamathon – Pilot Incubator on Somnia: The Dreamathon (our real-time dApps sprint) is live, turbocharging builders on the new Somnia L1 (think 1M+ TPS, sub-second finality). Over 8 weeks, 10 elite teams will hack towards real-time Web3 apps in SocialFi, DeFi, AI-driven info markets and more, with $200K in prizes and funding on the line. Apps are open now for a few wildcard slots (closing Aug 31) . Selected teams get up to $20K each, deep mentorship, and a shot at Somnia mainnet glory. Don’t sleep on this opportunity – if you’re building the next microsecond trading engine or attention economy app, we want to see it.
Axelar Infinity Quest – Mid-Program Update: Our cross-chain cohort with Axelar is hitting its stride at the halfway mark of the 8-week Infinity Quest. Ten teams received 75,000 $AXL each to build the next wave of interchain infrastructure . They’ve been diving into Axelar’s tech (General Message Passing, Interchain Token Service) and are already demoing early prototypes. From portable on-chain reputation (shoutout to Team Zeru bringing verifiable credentials to Axelar) to novel cross-chain DeFi primitives, you can feel the innovation coming off these companies. The program culminates soon with a showcase for investors and ecosystem partners. Keep an eye out for the demo day announcement, these projects could be the next killer app.
XDC “Vibe. Craft. Deploy. Pitch.” Bootcamp
XDC Network is running a free developer bootcamp in collaboration with VentureMiner and Cracked Labs—perfect for builders focused on UI design, AI agents, DeFi actions, and stablecoin payments.
Vibe. Craft. Deploy. Pitch. is structured as a 3-stage build sprint (August 27–29), culminating in a live pitch day on September 4.
Teams will deploy live apps on XDC and compete for $500 / $300 / $200 XDC prizes.
Themes: think AI-powered UIs, DeFi flows, and stablecoin integration.
This is a high-impact opportunity to ship a real demo, build in public, and pitch for seed-level capital, in under a week.
Why it matters: Perfectly aligns with our theme on smart, secure building—it pushes you to prototype live, embed best practices, and pitch with real infrastructure at your fingertips.
https://x.com/xdc_community/status/1955256494078758921
Cracked Alpha: Our Battle Codes competition is gearing up for launch. Prep your keyboards and your adrenaline – a bracket-style coding deathmatch is coming in hot (and yes, there will be prizes 🏆). Stay tuned… next week’s newsletter might just drop the bomb. Until then, BUIDL secure and crack on!